Businesses of all sizes have been investing in security software and fundamental cybersecurity infrastructure for decades. The antivirus industry has grown into a huge industry on its own from its humble beginnings of just being a small utility a user can optionally be bought and came with a floppy disk media. In fact, the very witness to this growth is Microsoft, as the OS developer officially published a list of 38 antivirus vendors that they certified as compatible with Windows.
The growth of the antivirus industry has been steady for a long time, as shown by the chart from Statistica: Security software revenue worldwide from 2011 to 2018 (2018 projected) in USD. There is no expectation for the industry to collapse anytime soon. The record shows that it will continue to grow linearly for years to come:
Security software revenue worldwide from 2011 to 2018 (2018 projected) in USD
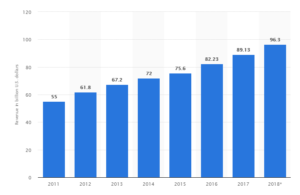
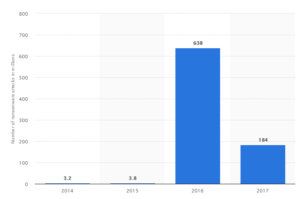
However, this linear growth is not credited to the antivirus vendors themselves, because this growth is just reactionary in nature. The increase of malware infection cases since 2016 was a heavy contributor to the acquisition of security products, as individuals and companies continue to look for the best defense against the risk to their data, getting hostage by malware. As evidenced by a Statistica report, although the cases of ransomware were less last year to the tune of 184 million incidents, it is still a huge number compared to 2015 which only had 3.8 million incidents recorded. The number of ransomware issues was record-breaking in 2016 when a whopping 638 million incidents were noted.
The annual number of ransomware attacks worldwide from 2014 to 2017 (in millions)
The first responders of a ransomware infection are the employees themselves. User education is vital, in order to isolate an incident of malware in the enterprise to minimize potential damage to the organization. It is critical for employees to become aware and always be alert when using corporate computers, as malware cannot easily penetrate a network without the aid of the users.
Below are some tips employees can do, the moment they notice something is wrong with their corporate desktop or laptop computers:
1. Immediately air-gap the suspicious/misbehaving computer
This means, quickly disconnect the computer from the network as soon as possible. The sooner the PC is isolated, any damage a virus may cause becomes restricted to just one computer instead of further spreading itself through the network.
2. Report to IT team immediately
End-users need to inform the IT team regarding their suspicions of the weird behavior of the computer being used. IT team has an internal protocol to follow when it comes to the incidents of malware infection and how to further mitigate the damage if there is one already. This report cannot be delayed, the sooner the IT team is notified, the better for the organization.
3. In case of lost data, check for availability of decryption keys from nomoreransom.org
Ransomware authors only have one target, to lock-out the user data and documents from the legitimate users through encryption. The IT team can check some resources online since some ransomware were already fully documented. One such service is nomoreransom.org, a non-profit site where various anti-malware vendors collectively reveal the decryption algorithms of the ransomware they were already aware of. If the ransomware is included in their list with known decrypters, a small utility is available for download that will automatically decrypt the encrypted files, undoing the damage the ransomware caused in the process.
4. Reformat the infected machine and restore data from the latest available backup. Never pay the ransom.
In the event that the ransomware is still new, and hence not yet documented by nomoreransom.org, please check the corporate backup system for the latest available backup to restore the lost data. These days there are many cloud-backup vendors and solutions are on the market. Operating a business without a backup system is unacceptable, given that many vendors such as Google, Microsoft and others offer cloud-backup services that range from free to a few tens of dollars per month/GB. Never pay the ransom demanded by the ransomware, as this will just motivate virus authors to continue developing more advanced future ransomware.
5. Keep Windows, Internet browser and plugins updated.
System administrators can set schedules for Windows Updates using the Group Policy component of Windows Active Directory server, while mainstream browsers like Firefox and Chrome automatically update themselves in the background once a newer version is available. Newer versions of plugins, like Java and Flash are also automated by their vendors. Using an old version of an Internet-facing application is risky, as malware authors take advantage of unfixed security bugs as a vector for infection.
Related Resources:
Fileless Ransomware is an Emerging Threat for U.S: Report
Ransomware Prevention Tips for the Healthcare Industry
Here’s A Warning To The Police: Ransomware Is The New Criminal
The Audacity Of WannaCry Ransomware Is A Warning Not To Ignore
